Featured
Table of Contents
- – Vpn Connections: How To Have Employees Work ...
- – What Is A Vpn And How Does It Work?
- – What Is A Vpn And Why Do I Need It?
- – Private Internet Access: The #1 Best Vpn Serv...
- – What Is A Vpn? Definition From Searchnetworking
- – Everything You Need To Know About Vpns For T...
- – What Is A Vpn & What Does It Do?
- – What Is A Vpn? Can You Describe How It Works?
Vpn Connections: How To Have Employees Work ...
In a mobile VPN, the server still sits at the edge of the organization's network, making it possible for safe tunneled gain access to by verified, licensed clients. Mobile VPN tunnels are not tied to physical IP addresses. Instead, each tunnel is bound to a sensible IP address. That rational IP address stays to the mobile device.
Hardware VPNs use a variety of benefits over software-based VPNs. In addition to offering improved security, hardware VPNs can provide load balancing for large customer loads. Administration is handled through a web internet browser interface. A hardware VPN is more expensive than a software-based one. Due to the fact that of the cost, hardware VPNs are more practical for larger companies.

Paid vendor choices tend to be suggested more frequently than complimentary ones. Some VPNvendors, amongst lots of, consist of the following: contains a strong collection of security functions with a big collection of servers. Nord, VPN has features such as Tor web browser connections for anonymous web surfing, while maintaining a strong position on client personal privacy.
What Is A Vpn And How Does It Work?
It does not provide too much in terms of extra features and personal privacy tools. Still, it is normally thought about an excellent VPN service. is a VPN service with a large and diverse set of distributed servers. It has strong privacy and details practices focused on security and offers additional features such as split tunneling.
VPNs are legal in the United States, however users and companies must inspect if they are legal in particular nations. Numerous VPNs use exceptionally comparable technologies, so it can be tough to choose which VPN will work best. Paid VPN services tend to be more trusted and include more security functions.
Around 2017, internet users in the United States learned that ISPs might collect and sell their browsing history, and net neutrality became a concept people needed to defend-- and effectively lost. An expense was gone by the U.S. Home of Representatives in 2019 to revive net neutrality, but was ultimately blocked by the Senate.
What Is A Vpn And Why Do I Need It?
With this understanding, using VPNs became a more genuine need for individuals.
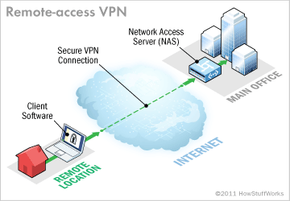
A VPN reroutes your traffic through a remote server, securing it in the procedure. Generally, when you try to access a site, your ISP (Internet Service Service provider) receives the request and reroutes you to your location. When you link to a VPN, it reroutes your web traffic through a remote server before sending it over to your location.
VPNs assist guarantee security anybody obstructing the encrypted information can't read it. Numerous years earlier, the most typical way to connect computers between multiple offices was by utilizing a rented line. Rented lines, such as ISDN (incorporated services digital network, 128 Kbps), are private network connections that a telecom company can rent to its clients.
Private Internet Access: The #1 Best Vpn Service For 10+ Years
These connections form a single wide-area network (WAN) for the company. Though rented lines are trustworthy and protected, the leases are costly, with expenses increasing as the distance in between workplaces boosts. Today, the web is more available than ever before, and internet service suppliers (ISPs) continue to develop faster and more reliable services at lower costs than leased lines.

Paid VPN services function very much like company VPNs however go through a VPN company to reach the web, rather than through a private company. These services are extremely simple to use. All you have to do is download the software, install it on your device, and connect to the server of your choice.
First, let's explore an analogy that describes how a VPN compares to other networking alternatives.
What Is A Vpn? Definition From Searchnetworking
All your internet traffic is routed through this tunnel to the server, which then sends out the traffic off to the public internet as usual. Information returning to your gadget makes the same journey: from the web, to the VPN server, through the encrypted connection, and back to your maker.
There are a few alternatives out there to establish your own, such as Outline. Doing so is relatively straightforward, but you'll either require to keep a server or lease one, which is less basic. While there are some efforts to make self-hosted VPNs more accessible, it's something best left to tinkerers who are eager to get their hands (digitally) unclean.
If you do not like that a company you're already paying is making money from your information or if you have issues about ISPs hoarding in-depth details about your activities, a VPN will help. Not even your ISP can see your web traffic when you use a VPN.VPNs also make it harder for advertisers and others to track you online.
Everything You Need To Know About Vpns For Travel In 2023
When the VPN is active, your real IP address is hidden, and anybody viewing you can just see the IP address of the VPN server. By hiding your real IP address, VPNs reject snoops one tool used to recognize and track you online. In spite of that, VPNs do not make you completely anonymous online.

Some VPN services consist of devoted antivirus tools also, and some anti-viruses companies now offer VPNs. We don't typically evaluate the malware-detecting abilities of VPNs, considering that we see VPNs mostly as a privacy service. To resolve the threat of malware, our company believe standalone anti-malware softwarewhether it's one you buy or the one that ships with your computerdoes a much better job.
A VPN will conceal the contents of your web traffic from some observers and can make it harder for you to be tracked online. But a VPN can, at best, provide just limited defense versus the threats you're most likely to encounter on the internet: malware, social engineering rip-offs, and phishing websites.
What Is A Vpn & What Does It Do?
All your internet traffic is routed through this tunnel to the server, which then sends the traffic off to the public internet as normal. Data returning to your gadget makes the very same trip: from the internet, to the VPN server, through the encrypted connection, and back to your device.
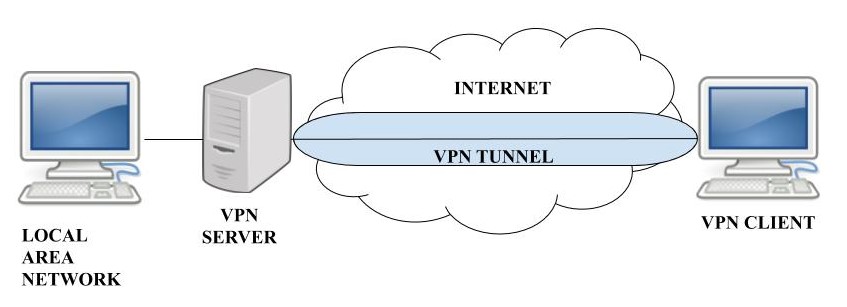
There are a couple of options out there to set up your own, such as Overview. Doing so is relatively simple, but you'll either need to keep a server or lease one, which is less basic. While there are some efforts to make self-hosted VPNs more accessible, it's something best left to tinkerers who aspire to get their hands (digitally) unclean.
If you do not like that a company you're already paying is benefiting from your information or if you have issues about ISPs hoarding comprehensive info about your activities, a VPN will help. Not even your ISP can see your web traffic when you use a VPN.VPNs also make it harder for marketers and others to track you online.
What Is A Vpn? Can You Describe How It Works?
When the VPN is active, your true IP address is hidden, and anyone watching you can just see the IP address of the VPN server. By hiding your genuine IP address, VPNs reject snoops one tool used to recognize and track you online. Regardless of that, VPNs do not make you completely anonymous online.
Some VPN services include devoted anti-virus tools as well, and some anti-viruses business now use VPNs. We don't generally check the malware-detecting abilities of VPNs, since we view VPNs mostly as a personal privacy service. To attend to the threat of malware, our company believe standalone anti-malware softwarewhether it's one you buy or the one that ships with your computerdoes a much better job.
A VPN will hide the contents of your web traffic from some observers and can make it harder for you to be tracked online. However a VPN can, at best, provide only restricted defense against the risks you're more than likely to experience online: malware, social engineering frauds, and phishing websites.
Table of Contents
- – Vpn Connections: How To Have Employees Work ...
- – What Is A Vpn And How Does It Work?
- – What Is A Vpn And Why Do I Need It?
- – Private Internet Access: The #1 Best Vpn Serv...
- – What Is A Vpn? Definition From Searchnetworking
- – Everything You Need To Know About Vpns For T...
- – What Is A Vpn & What Does It Do?
- – What Is A Vpn? Can You Describe How It Works?
Latest Posts
Best Vpn For Business
18 Best Vpn Services To Protect Your Online Privacy + ...
Best Virtual Private Networks Reviews 2023
More
Latest Posts
Best Vpn For Business
18 Best Vpn Services To Protect Your Online Privacy + ...
Best Virtual Private Networks Reviews 2023